This article was authored by Mike Bittner, Associate Director of Digital Security & Operations.
Malware designed to outsmart blockers and AVs
Supply chain attacks continue to bedevil digital advertising with no sign of abating. The attacks are not only scaling up in size, but ramping up their offensive ingenuity. In March, 200+ premium publishers came under attack by what The Media Trust’s Digital Security & Operations (DSO) team believes to be the same perpetrators behind February’s ShapeShifter-3PC campaign. This latest phishing attack exploited several well-known ad networks, used frequent code switching, alternated among more than 30 malicious domains to outsmart signature-based defenses, and spoofed online payment tools.
Adjustments on offense takes campaign sophistication to the next level
The group behind the attack appear to have sharpened their saws since ShapShifter-3PC. Named “Red Baron” by the DSO, the cybercrime group demonstrated deepening insights into the digital ad supply chain. They exploited well-known ad networks, in particular two buy-side platforms notorious for lax security. The DSO traced most of the more than 50,000 related incidents (each one affecting thousands of users) back to these two platform providers. Visitors to the affected publications would receive one of two types of scams, depending on their device.
The scam perpetrated by the malware, dubbed “AfterShock-3PC” by the DSO, would unfold over the course of several steps. Windows users would receive fraudulent pop-up warnings to renew their antivirus software. A ransomware pop-up message would quickly follow, threatening users with file encryption if they fail to renew within 15 minutes. Those who clicked to renew would be redirected to a malicious landing page masquerading as a known online payment platform. Some were given the option to pay the $150 renewal fee in bitcoins. Any information that users entered would be sent to a command and control server. Those who chose not to renew within the 15-minute countdown would find their browsers frozen and would have to restart their machines, at which point the malware would exit and leave no digital traces behind. Mobile device users would receive a phony $1,000 pop-up gift card from a top retailer and be instructed to enter their email address, physical address, annual income, and gender. Information from any of the infected users would likely be sold to parties who profit from the trade in consumers’ information on the dark web.
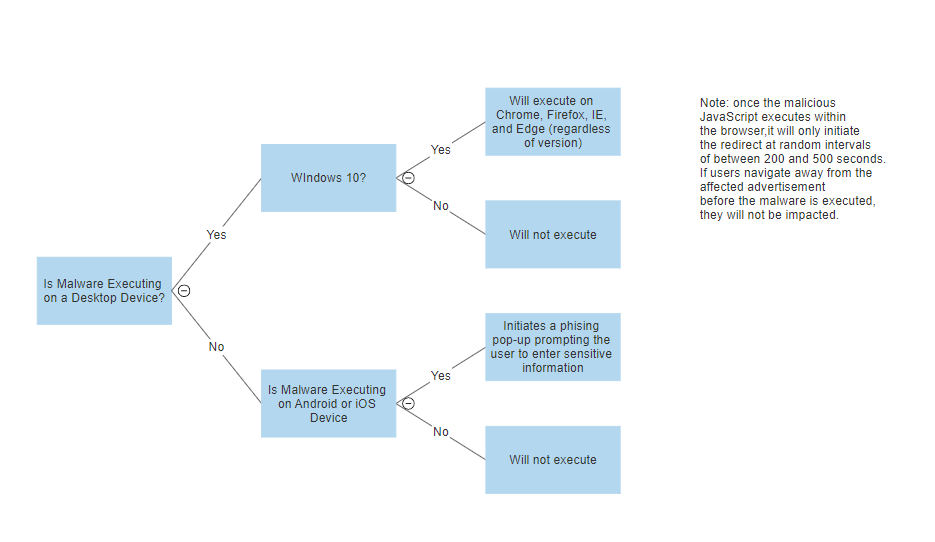
Malware style analysis
The DSO was able to stop the attack through a combination of continuous scanning, smart blockers, and behavioral analysis. Initially tipped off by the bad actors’ use of many of the same domains linked to the ShapeShifter-3PC campaign, the DSO team alerted affected clients and stopped the malware from reaching their digital readers. They were especially struck by the distinctive insertion of commentary within the polymorphic malware’s code. The malware’s ability to escape signature detection through clever nuances within the code marks a significant stride in technique for malvertising groups, who typically rely on simple obfuscation or recycled code.
The DSO confirmed that this attack slipped through signature defenses like conventional blockers fed with third party data (once a day at most). When bad actors go on unprecedented offense with malware that can frequently switch code and domains, only a layered approach that includes experts who can spot and verify unknown and obfuscated malicious code, machine-learning assisted scanning that continuously looks out for anomalous activity, and collaborating with the digital supply chain is a publishers’ most effective defensive move.
The Media Trust notified Federal authorities of the attack and provided extensive information.
Smarter attacks require a smarter approach
Attack campaigns are not what they used to be; nor should the tools to thwart them. Since the beginning of 2019, the DSO has seen growing use of adaptive attacks and polymorphous malware designed to outsmart conventional defenses that can only stop known threats. However, today’s malware is more often new and unknown than known, and can renew itself through code changes. No single, simple solution can protect the user experience from such sophisticated campaigns. If anything, defenses based on signatures alone enable the spread of today’s more pernicious malware.

