
This article was authored by Pat Ciavolella, Director, Digital Security & Operations, The Media Trust.
A large-scale ad stacking incident involving in-app video impressions is affecting dozens of premium digital advertising technology providers and media publishers. Ad stacking or stuffing is an ad fraud technique where multiple ads are piled on top of each other within the same slot. While the user sees only the top ad, the succeeding ad layers that remain invisible to the user are charged to the advertiser as viewed impressions.
Ad fraud by another name
While ad stacking is not new, this current situation is unique for surging to more than 10,000 ad tags in the digital ecosystem in only four days. This incident involves in-app video ads, frequently making up to 10 calls for these high-value ads in the mobile environment.
The incentive is to serve as many ads as possible and earn money. Taking advantage of programmatic advertising, the bad actor injects multiple ads into a campaign and charges the buyer for impressions when only a small fraction of impressions was viewed by humans—generating unearned revenue. Ad stacking also hurts publishers by driving down their viewability metrics, and, as a result, eroding their reputation with advertisers. In addition, continuous calls for these ads that don’t earn revenue cause unnecessary latency to the user.
How it works
The current incident started on June 6, the fraudster slowly tested the use of 6 different domain pairs by placing campaigns with at least 3 DSPs that feed into dozens of exchanges and SSPs, and eventually executing in the mobile apps of 10 newspaper publishers which use popular SDKs for their app environment.
When the specific domain combination executes it loads a placeholder static image (i.e., visible to the user. Image 1) while a video ad renders in the background and continues to make calls. (Image 2) For now, the fraud targets ads on the main or home screen and comics areas of the mobile apps.

Image 1: Placeholder creative from legitimate campaigns
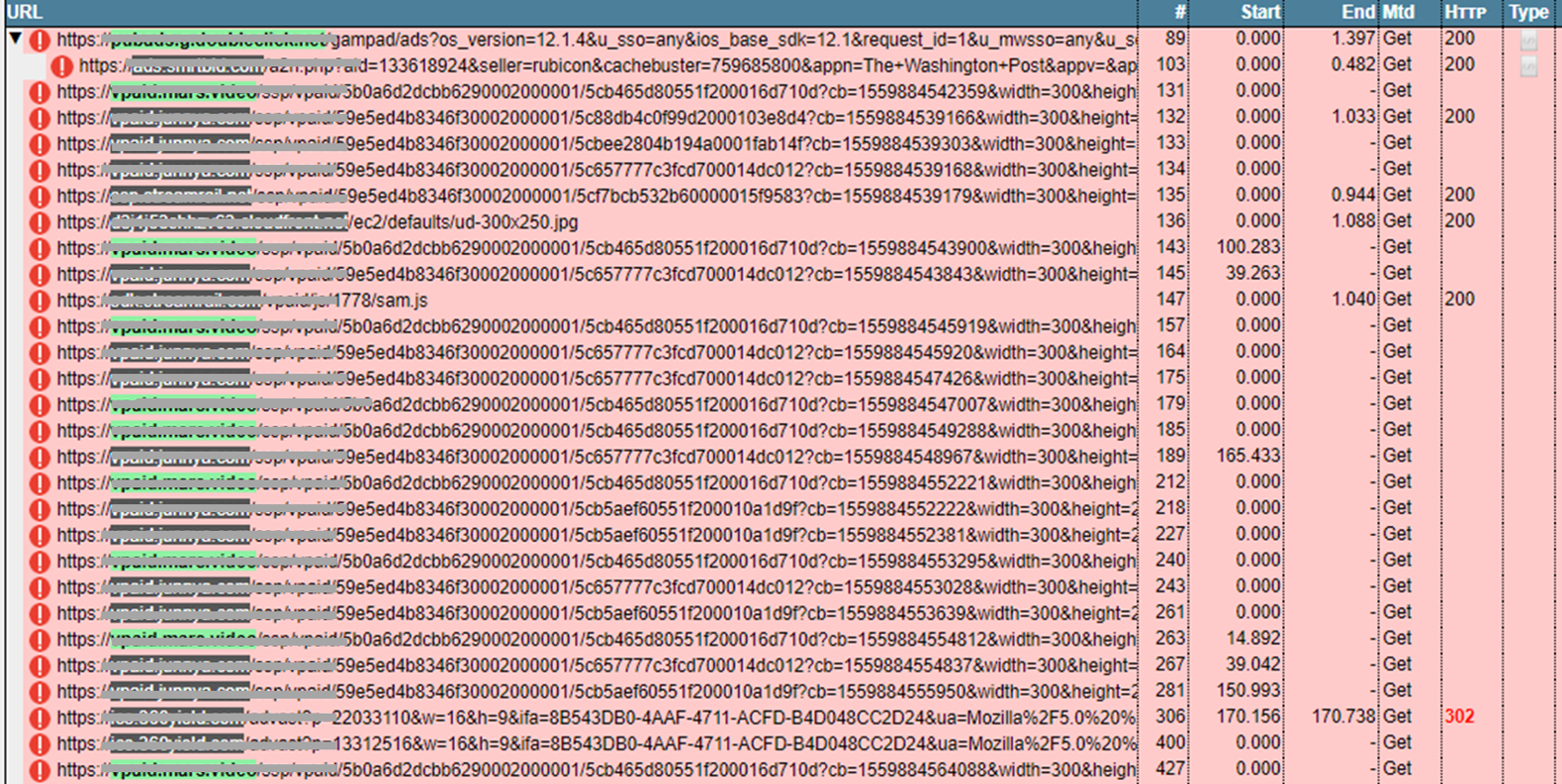
Image 2: Example of continuous calls made in one user session
The industry challenge
This incident is interesting due to its quickly escalating nature in a high-value advertising revenue environment—video ads and mobile apps. What makes this incident difficult to control is how it’s executed. It’s important to keep in mind that the domains themselves (i.e., domain.com) are from valid digital partners; it’s the specific urls (i.e., domain.com/badstuffurl) when used in combination that are responsible for perpetrating the ad fraud—a distinction that The Media Trust notes for our clients.
With 45% of digital budgets being spent on mobile (both web and app) and programmatic as the preferred channel, in-app spend is projected to best $77 billion this year. Ad stacking represents significant harm to the industry. Assuming the average in-app programmatic video ad costs $20 CPM, this incident means a buyer could spend $2M for 100 million impressions but only receive 10 million impressions which should only cost $200,000. The bad actor is poised to earn thousands of dollars in the next few days.
The good news is that the incident has been isolated to a specific buyer on the 3 DSPs, who have been notified to block the campaign and remove the buyer from their platforms. As a result, the number of detected incidents has significantly slowed in the past 12 hours.
Next Steps for ad tech and publishers
The Media Trust considers ad stacking a problem due to its ability to create a bad user experience and enable advertising fraud and should not be allowed in the digital environment. Detected via extensive scanning of video ads and mobile apps, The Media Trust immediately notified affected clients and instructed to terminate the offending urls with their upstream partners. In addition, Media Filter users can create a Custom Block on the offending urls and closely monitor impressions and revenue impact; you’ll want to remove the block when the incident is fully resolved.



